issue_comments
16 rows where author_association = "OWNER" and issue = 633578769 sorted by updated_at descending
This data as json, CSV (advanced)
Suggested facets: created_at (date), updated_at (date)
issue 1
- Support "allow" block on root, databases and tables, not just queries · 16 ✖
| id | html_url | issue_url | node_id | user | created_at | updated_at ▲ | author_association | body | reactions | issue | performed_via_github_app |
|---|---|---|---|---|---|---|---|---|---|---|---|
| 640362879 | https://github.com/simonw/datasette/issues/811#issuecomment-640362879 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDM2Mjg3OQ== | simonw 9599 | 2020-06-08T04:42:28Z | 2020-06-08T13:39:46Z | OWNER | I'm finding myself repeating this pattern a lot:
An abstraction around this would be useful. Idea:
|
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640367128 | https://github.com/simonw/datasette/issues/811#issuecomment-640367128 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDM2NzEyOA== | simonw 9599 | 2020-06-08T05:00:13Z | 2020-06-08T05:00:49Z | OWNER | Should the padlock show up on tables that are private only because they inherited their privacy from their parent database or even the parent instance? Interesting question. If an instance is private, I'm not sure it makes sense to show padlocks on absolutely everything. Likewise, a list of tables shown on the database table with a padlock next to every single table (when the database itself is private) doesn't seem to add any useful information. I think "Show 🔒 in header on private database page" will resolve this for me. I'll always show the padlock in the header of a database/table page even if that privacy is inherited - but I won't do that for padlocks shown in the list of tables or list of databases. |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640365512 | https://github.com/simonw/datasette/issues/811#issuecomment-640365512 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDM2NTUxMg== | simonw 9599 | 2020-06-08T04:53:49Z | 2020-06-08T04:53:49Z | OWNER | I really like the padlocks. I should include a screenshot in the documentation that illustrates them.
Maybe I should figure out a way to have the https://latest.datasette.io/ demo illustrate both a logged-in and a logged-out state. |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640348785 | https://github.com/simonw/datasette/issues/811#issuecomment-640348785 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDM0ODc4NQ== | simonw 9599 | 2020-06-08T03:51:50Z | 2020-06-08T03:51:50Z | OWNER | New convention: the 🔒 icon is now shown next to resources that are private - that are visible to you now, but would not be visible to the anonymous user.
|
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640345115 | https://github.com/simonw/datasette/issues/811#issuecomment-640345115 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDM0NTExNQ== | simonw 9599 | 2020-06-08T03:37:33Z | 2020-06-08T03:37:33Z | OWNER | Per-table permissions is pretty interesting for large installations though - an organization might have hundreds of CSV files imported into Datasette and then allow users to specify which exact users within that organization are allowed to see which CSV. |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
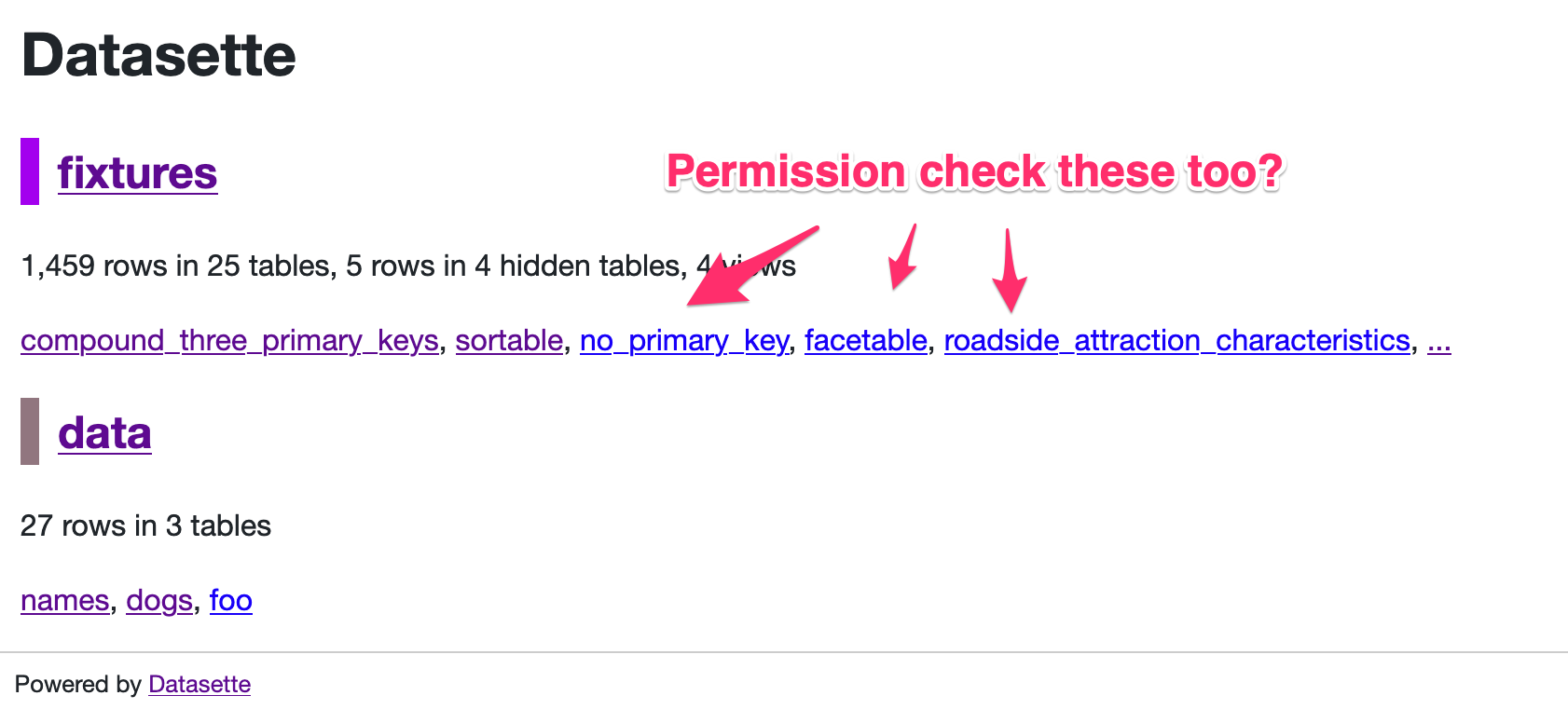
| 640344950 | https://github.com/simonw/datasette/issues/811#issuecomment-640344950 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDM0NDk1MA== | simonw 9599 | 2020-06-08T03:36:49Z | 2020-06-08T03:36:49Z | OWNER | Oh this is a bit awkward - should I be running per-table permission checks for every table that might be shown on the index page?
|
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640339674 | https://github.com/simonw/datasette/issues/811#issuecomment-640339674 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDMzOTY3NA== | simonw 9599 | 2020-06-08T03:18:15Z | 2020-06-08T03:18:15Z | OWNER | I should take these permissions into account when displaying a list of tables or a list of databases (like I do right now when displaying a list of queries). |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640338347 | https://github.com/simonw/datasette/issues/811#issuecomment-640338347 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDMzODM0Nw== | simonw 9599 | 2020-06-08T03:13:23Z | 2020-06-08T03:13:23Z | OWNER | Do row-level permissions even make sense? Might be a good idea to remove those until I have a good use-case for them. |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640338151 | https://github.com/simonw/datasette/issues/811#issuecomment-640338151 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDMzODE1MQ== | simonw 9599 | 2020-06-08T03:12:41Z | 2020-06-08T03:12:41Z | OWNER | Also need to expand the docs on https://datasette.readthedocs.io/en/latest/authentication.html to explain where you can put |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640337951 | https://github.com/simonw/datasette/issues/811#issuecomment-640337951 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDMzNzk1MQ== | simonw 9599 | 2020-06-08T03:11:58Z | 2020-06-08T03:11:58Z | OWNER | I'd like to be able to apply permissions for the ability to run a SQL query - but I'm not sure where the best place for that |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640287967 | https://github.com/simonw/datasette/issues/811#issuecomment-640287967 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDI4Nzk2Nw== | simonw 9599 | 2020-06-07T22:16:10Z | 2020-06-07T22:16:10Z | OWNER | The tests in test_permissions.py could check the .json variants and assert that permission checks were carried out too. |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640274171 | https://github.com/simonw/datasette/issues/811#issuecomment-640274171 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDI3NDE3MQ== | simonw 9599 | 2020-06-07T20:21:14Z | 2020-06-07T20:21:14Z | OWNER | Next step: fix this
|
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640273945 | https://github.com/simonw/datasette/issues/811#issuecomment-640273945 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDI3Mzk0NQ== | simonw 9599 | 2020-06-07T20:19:15Z | 2020-06-07T20:19:15Z | OWNER | I'm going to add a |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640270178 | https://github.com/simonw/datasette/issues/811#issuecomment-640270178 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDI3MDE3OA== | simonw 9599 | 2020-06-07T19:48:39Z | 2020-06-07T19:48:39Z | OWNER | Testing pattern:
|
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640248972 | https://github.com/simonw/datasette/issues/811#issuecomment-640248972 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDI0ODk3Mg== | simonw 9599 | 2020-06-07T17:04:22Z | 2020-06-07T17:04:22Z | OWNER | I'll need a neat testing pattern for this. |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 | |
| 640248669 | https://github.com/simonw/datasette/issues/811#issuecomment-640248669 | https://api.github.com/repos/simonw/datasette/issues/811 | MDEyOklzc3VlQ29tbWVudDY0MDI0ODY2OQ== | simonw 9599 | 2020-06-07T17:01:44Z | 2020-06-07T17:01:44Z | OWNER | If the allow block at the database level forbids access this needs to cascade down to the table, query and row levels as well. |
{
"total_count": 0,
"+1": 0,
"-1": 0,
"laugh": 0,
"hooray": 0,
"confused": 0,
"heart": 0,
"rocket": 0,
"eyes": 0
} |
Support "allow" block on root, databases and tables, not just queries 633578769 |
Advanced export
JSON shape: default, array, newline-delimited, object
CREATE TABLE [issue_comments] (
[html_url] TEXT,
[issue_url] TEXT,
[id] INTEGER PRIMARY KEY,
[node_id] TEXT,
[user] INTEGER REFERENCES [users]([id]),
[created_at] TEXT,
[updated_at] TEXT,
[author_association] TEXT,
[body] TEXT,
[reactions] TEXT,
[issue] INTEGER REFERENCES [issues]([id])
, [performed_via_github_app] TEXT);
CREATE INDEX [idx_issue_comments_issue]
ON [issue_comments] ([issue]);
CREATE INDEX [idx_issue_comments_user]
ON [issue_comments] ([user]);


user 1